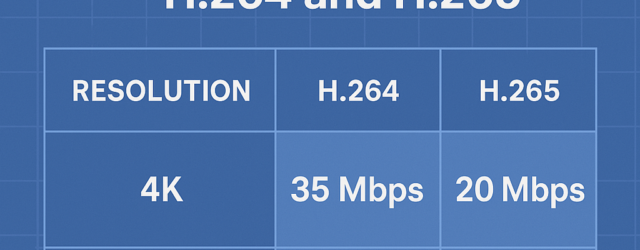
Video Encoding Bitrates for 4K and 1080p with H.264 and H.265
Understanding H.264 and H.265 H.264, also known as Advanced Video Coding (AVC), is a widely adopted codec known for its balance between compression efficiency and compatibility. It has been the standard for many 1080p video applications but can struggle with… Continue Reading