How to Install TURN Server on Ubuntu For WebRTC
In this article you will learn how to install TURN Server on Ubuntu 20.04 LTC for WebRTC, configure Coturn with Long Term Credential Mechanism, configure IPTables firewall, check TURN server.
The TURN server implements the STUN protocol also.
Coturn is free open source TURN server.
Requirements
To install Coturn Server minimum you will need:
- Installed minimal Ubuntu server 20.04 LTS (or never)
- Public IP for your your server
- SSL Certificates for the sub-domains (in this guide we will generate free Letsencrypt SSL certificate)
Installing Coturn Server In Ubuntu/Debian
To install Coturn Server in Ubuntu 20.04 LTS run:
$ sudo apt-get update $ sudo apt-get install openssl coturn
Configuring Coturn
Before start configuring TURN server backup your original Coturn configuration file:
$ sudo cp /etc/turnserver.conf /etc/turnserver.orig
Generating TLS Certificates
To generate free TLS certificates for out TURN Server we will use certbot tool from Let’s Encrypt.
$ sudo apt-get -y update
$ sudo apt-get -y install certbot
Then run a certbot command for generate the certificate:
$ sudo certbot certonly --standalone
Wizard will ask your email and server domain name.
Example output:
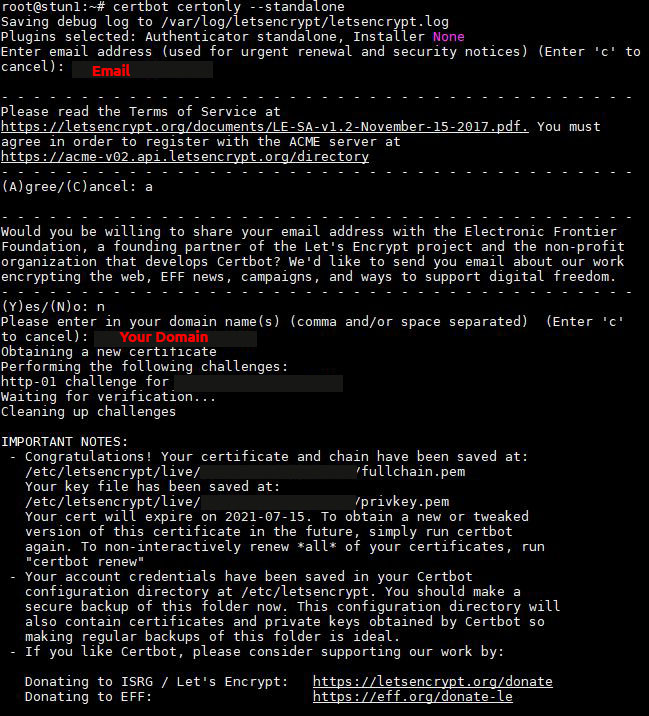
If everything fine, your brand new generated SSL/TLS certificates you can found in /etc/letsencrypt/live/YOUR_DOMAIN directory.
To generate a DH file 2048 bit using OpenSSL run (can take long time):
$ cd /etc/letsencrypt/live/YOUR_DOMAIN/
$ sudo openssl dhparam -out dhparam.pem 2048
Now add flowing lines into your TURN Server config file – /etc/turnserver.conf:
server-name=YOUR_DOMAIN cert=/etc/letsencrypt/live/YOUR_DOMAIN/cert.pem pkey=/etc/letsencrypt/live/YOUR_DOMAIN/privkey.pem dh-file=/etc/letsencrypt/live/YOUR_DOMAIN/dhparam.pem cipher-list="ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384"
TURN Server Configuration
Fill /etc/turnserver.conf with next config, replace with your real, IP, username and passwords:
# Replace with the realm of you server realm=YourServerRealm fingerprint listening-ip=0.0.0.0 # Replace with your TURN server external IP external-ip=SERVER_EXTERNAL_IP listening-port=3478 tls-listening-port=5349 min-port=32769 max-port=65535 log-file=/var/log/turnserver.log verbose no-cli no-loopback-peers no-multicast-peers cert=/etc/letsencrypt/live/YOUR_DOMAIN/cert.pem pkey=/etc/letsencrypt/live/YOUR_DOMAIN/privkey.pem dh-file=/etc/letsencrypt/live/YOUR_DOMAIN/dhparam.pem cipher-list="ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384" #Long Term Credential Mechanism authentication lt-cred-mech user1=username1:password1 user2=username2:password2
Stop/Start Coturn Server
$ sudo systemctl status coturn $ sudo systemctl start coturn $ sudo systemctl stop coturn $ sudo systemctl restart coturn
Run Coturn at Startup
To enable Coturn auto-start at boot time:
$ sudo systemctl enable coturn
Check Coturn Service
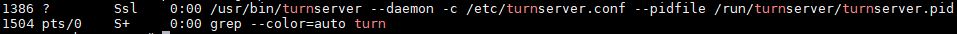
Check if the service Coturn is running:
$ sudo ps -ax | grep turn
Example output:
Test Coturn Server
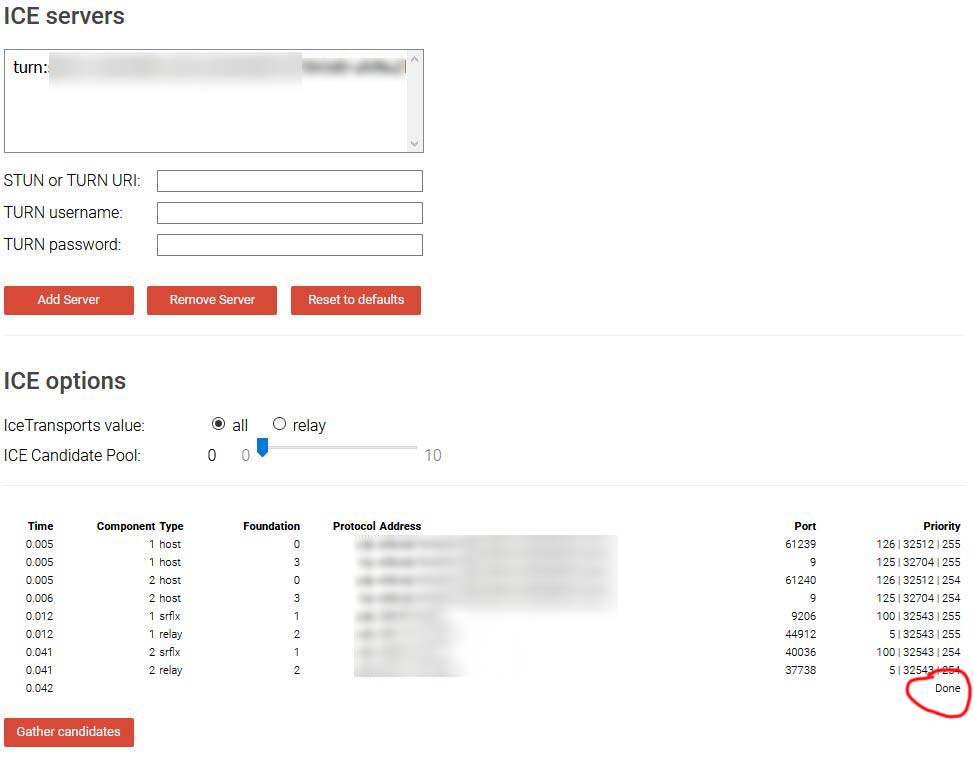
To test Coturn server configuration use free service Trickle ICE for testing TURN/STUN servers. It will create a connections with the specified TURN/ICE Servers, and then starts candidate gathering for a session with a single audio stream.
Enter your STUN or TURN URI, TURN username, TURN password, Add Server, then push “”Gather candidates” button.
If your TURN/STUN server is configured correctly, then at the end you should see: DONE.
As shown in example output:
TURN Server Ports
The default ports for STUN and TURN servers using by WebRTC are:
| HTTP/HTTPS | TCP | 80/443 |
| TURN/STUN | TCP, UDP | 3478 |
| TURN TLS | TCP, UDP | 5349 |
| TURN Relay | UDP | 32768-65535 |
Configure IPtables Firewall for using TURN
Clear IPtables rules: # iptables -P INPUT ACCEPT # iptables -F # iptables -X
Insert rules firewall rules for TURN server:
# iptables - -A INPUT -i lo -j ACCEPT # iptables --A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT # iptables --A INPUT -s Your_IP -p tcp -m tcp --dport 22 -m state --state NEW -m comment --comment "Alow SSH from your IP " -j ACCEPT # iptables --A INPUT -p tcp -m tcp --dport 80 -j ACCEPT # iptables --A INPUT -p udp -m udp --dport 443 -j ACCEPT # iptables --A INPUT -p tcp -m tcp --dport 3478 -j ACCEPT # iptables --A INPUT -p udp -m udp --dport 3478 -j ACCEPT # iptables --A INPUT -p tcp -m tcp --dport 5349 -j ACCEPT # iptables --A INPUT -p udp -m udp --dport 5349 -j ACCEPT # iptables --A INPUT -p udp -m udp --dport 49152:65535 -j ACCEPT # iptables -P INPUT DROP # iptables -P FORWARD DROP # iptables -P OUTPUT ACCEPT
If you don’t have iptables-persistent install it:
$ sudo apt-get install iptables-persistent
Discuss article in ArsTech Forum
If you like what you are reading, please:
 Buy me a coffee
Buy me a coffee





