CentOS Firewalld. How To
CentOS firewalld provides a dynamically managed firewall with support for network/firewall zones to define the trust level of network connections or interfaces. It has support for IPv4, IPv6 firewall settings and for ethernet bridges and has a separation of runtime and permanent configuration options. It also supports an interface for services or applications to add firewall rules directly.
Start/Stop Firewalld Service
# systemctl start firewalld # systemctl stop firewalld
Enable/Disable Firewalld Service On Boot
# systemctl enable firewalld # systemctl disable firewalld
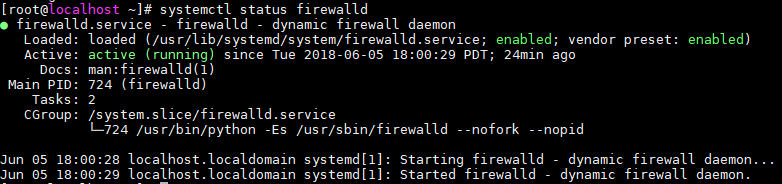
Check Status Of The Firewalld Daemon
# systemctl status firewalld
View The Default Zone
# firewall-cmd --get-default-zone
Change The Default Zone
# firewall-cmd --set-default-zone=internal
Check The Zones Assigned To The Network Interfaces
# firewall-cmd --get-active-zones
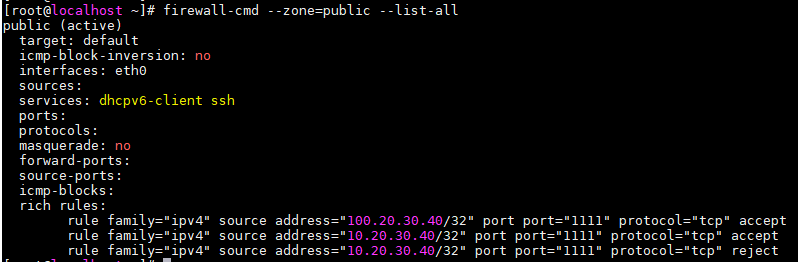
Get Configuration For A Specific Zone
# firewall-cmd --zone=public --list-all # firewall-cmd --list-service
Get Configuration For All Zones
# firewall-cmd --list-all-zones
Reload Firewalld Rules
Reload firewalld rules, current permanent configuration will become new runtime configuration. All runtime only changes done until reload are lost with reload if they have not been also in permanent configuration.
# firewall-cmd --reload
Services
Default defined services directory located in folder: /usr/lib/firewalld/services
Show Default Defined Services:
firewall-cmd --get-services
Add or Remove The Service, Reload Firewalld
# firewall-cmd --add-service=http # firewall-cmd --remove-service=http # firewall-cmd --zone=public --add-service=ssh --permanent # firewall-cmd --zone=public --remove-service=ssh --permanent # firewall-cmd --reload
Allowing or Denying an Port and Protocol
# firewall-cmd --zone=public --add-port=8080/tcp --permanent # firewall-cmd --zone=public --remove-port=8080/tcp --permanent # firewall-cmd --reload # firewall-cmd --add-port=25/tcp # firewall-cmd --remove-port=25/tcp # firewall-cmd --list-port
Rich Rules
With the rich language more complex firewall rules can be created in an easy to understand way. The rich language extends the current zone elements (service, port, icmp-block, icmp-type, masquerade, forward-port and source-port) with additional source and destination addresses, logging, actions and limits for logs and actions.
List Current Rich Rules
# firewall-cmd --list-rich-rules
Adding/Blocking specific IP Address
# firewall-cmd --zone=public --add-rich-rule='rule family="ipv4" source address="1.2.3.4" accept' # firewall-cmd --zone=public --add-rich-rule='rule family="ipv4" source address="1.2.3.4" reject'
Allow/Deny TCP Traffic From Specific IP address To Specefic Port. Add Rich Rule
# firewall-cmd --permanent --zone=public --add-rich-rule=' rule family="ipv4" source address="10.20.30.40/32" port protocol="tcp" port="1111" accept' # firewall-cmd --permanent --zone=public --add-rich-rule=' rule family="ipv4" source address="10.20.30.40/32" port protocol="tcp" port="1111" reject' # firewall-cmd --reload
Remove Rich Rule
To remove added rule, replace the –add-rich-rule with remove –remove-rich-rule:
# firewall-cmd --permanent --zone=public --remove-rich-rule=' rule family="ipv4" source address="10.20.30.40/32" port protocol="tcp" port="1111" accept'
How To Disable Iptables Firewall In CentOS 7
# systemctl stop iptables # systemctl disable iptables # systemctl mask iptables